Cybersecurity & EDR Solutions
Small businesses face enterprise-grade threats—ransomware, phishing, remote-access exploits, and insider risk.
Our Cybersecurity & Endpoint Detection & Response (EDR) program delivers 24/7 protection, compliance
readiness, and clear reporting so you can operate with confidence.
What you can expect
- Managed EDR/XDR with rollback & guided remediation
- Hardening for firewalls, identity, email, and remote access
- Patch/vulnerability management and prioritized fixes
- Awareness training and phishing simulations
- Continuous monitoring with incident response support
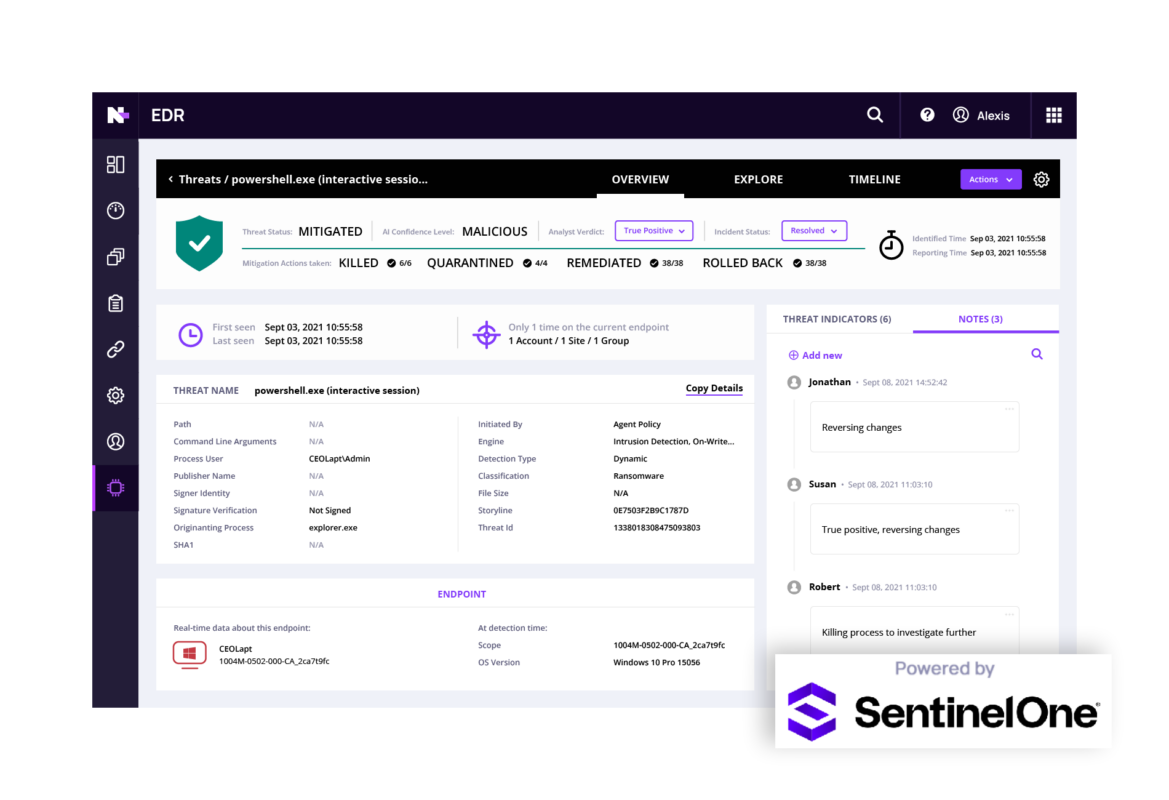 Real-time detections, rollback, and response workflows.
Real-time detections, rollback, and response workflows.
Compliance Support
Aiming for HIPAA, PCI-DSS, SOC 2, or internal standards? We align your controls and documentation to modern
requirements, perform technical assessments, and close gaps—so audits and carrier questionnaires are painless.
- Policy packs (access, MFA, encryption, IR, retention, BYOD)
- Evidence collection & reporting for audits and insurance
- Table-top exercises and incident communications playbooks